To protect your endpoints with the Bitdefender security agent, you must install it on each of them.
Once you have installed a Relay agent, it will automatically detect unprotected endpoints in the same network.
The Bitdefender protection can then be installed on endpoints remotely from Control Center.
Remote installation is performed in the background, without the user knowing about it.
Warning
Before installation, be sure to uninstall existing antimalware and firewall software from computers.
Installing the Bitdefender protection over existing security software may affect their operation and cause major problems with the system.
Windows Defender and Windows Firewall will be turned off automatically when installation starts.
If you want to deploy the security agent on a computer with Bitdefender Antivirus for Mac 5.X, you first must remove the latter manually. For the guiding steps, refer to Deploy Endpoint Security for Mac on a machine with Bitdefender Antivirus for Mac 5.X.
When deploying the agent through a Linux Relay, the following conditions must be met:
The Relay endpoint must have installed the Samba package (
smbclient) version 4.1.0 or above and thenetbinary/command to deploy Windows agents.The
netbinary/command is usually delivered with the samba-client and / or samba-common packages. On some Linux distributions (such as CentOS 7.4), thenetcommand is only being installed when installing the full Samba suite (Common + Client + Server). Make sure that your Relay endpoint has thenetcommand available.Target Windows endpoints must have Administrative Share and Network Share enabled.
Target Linux and Mac endpoints must have SSH enabled and firewall disabled.
To run a remote installation task:
Connect and log in to Control Center.
Go to the Network page.
Select the desired group from the left-side pane.
The entities contained in the selected group are displayed in the right-side pane table.
Optionally, you can apply filters to display unmanaged endpoints only. Click the Filters menu and select the following options: Unmanaged from the Security tab and All items recursively from the Depth tab.
When working with EC2 instances, you can also add the EC2 Instances option in the Type tab, while applying all the other above mentioned criteria.
Select the entities (endpoints or groups of endpoints) on which you want to install protection.
Click the
 Tasks button at the upper side of the table and choose Install.
Tasks button at the upper side of the table and choose Install.The Install Client wizard is displayed.

Under Options section, configure the installation time:
Now, to launch the deployment immediately.
Scheduled, to set up the deployment recurrence interval. In this case, select the time interval that you want (hourly, daily or weekly) and configure it according to your needs.
For example, when certain operations are required on the target machine before installing the client (such as uninstalling other software and restarting the OS), you can schedule the deployment task to run every 2 hours. The task will start on each target machine every 2 hours until the deployment is successful.
If you want target endpoints to automatically restart for completing the installation, select Automatically reboot (if needed).
Under the Credentials Manager section, specify the administrative credentials required for remote authentication on target endpoints. You can add the credentials by entering the user and password for each target operating system.
Important
For Windows 8.1 stations, you need to provide the credentials of the built-in administrator account or a domain administrator account. To learn more, refer to Client software deployment on Windows 8.1/10/2012 and above.
To add the required OS credentials:
Enter the user name and password of an administrator account in the corresponding fields from the table header.
If computers are in a domain, it suffices to enter the credentials of the domain administrator.
Use Windows conventions when entering the name of a user account:
For Active Directory machines use these syntaxes:
username@domain.comanddomain\username. To make sure that entered credentials will work, add them in both forms (username@domain.comanddomain\username).For Workgroup machines, it suffices to enter only the user name, without the workgroup name.
Optionally, you can add a description that will help you identify each account more easily.
Enter the user name of an administrator account in the corresponding fields from the table header.
Use Windows conventions when entering the name of a domain user account, for example,
user@domain.comordomain\user. To make sure that entered credentials will work, add them in both forms (user@domain.comanddomain\user).Note
If computers are in a domain, it suffices to enter the credentials of the domain administrator.
Use Windows conventions when entering the name of a domain user account, for example,
user@domain.comordomain\user. To make sure that entered credentials will work, add them in both forms (user@domain.comanddomain\user).Select the authentication type from the menu:
Password, to use the administrator’s password.
Upload .pem file, to use a private key.
If you authenticate using a password, enter the password in the field next to the menu.
If you authenticate using a private key, click the Browse button and select the
.pemfile containing the corresponding private key.Optionally, you can add a description that will help you identify each account more easily.
Click the
 Add button. The account is added to the list of credentials.
Add button. The account is added to the list of credentials.Specified credentials are automatically saved to your Credentials Manager so that you do not have to enter them the next time. To access the Credentials Manager, just point to your username in the upper-right corner of the console.
Important
If the provided credentials are invalid, the client deployment will fail on the corresponding endpoints. Make sure to update the entered OS credentials in the Credentials Manager when these are changed on the target endpoints.
Select the check boxes corresponding to the accounts you want to use.
A warning message is displayed as long as you have not selected any credentials. This step is mandatory to remotely install the security agent on endpoints.
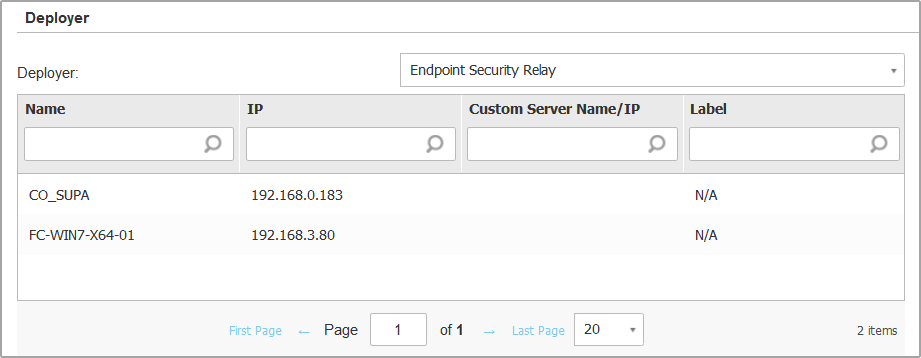
Under Deployer section, configure the Relay to which the target endpoints will connect for installing and updating the client:
All machines with Relay role detected in your network will show-up in the table available under the Deployer section. Each new client must be connected to at least one Relay client from the same network, that will serve as communication and update server. Select the Relay that you want to link with the target endpoints. Connected endpoints will communicate with Control Center only via the specified Relay.
Important
Port 7074 must be open, for the deployment through the Relay agent to work.

If target endpoints communicate with the Relay agent via proxy, you also need to define the proxy settings. In this case, select Use proxy for communication and enter the required proxy settings in the fields below.
You need to select one installation package for the current deployment. Click the Use package list and select the installation package that you want. You can find here all the installation packages previously created for your account and also the default installation package available with Control Center.
If needed, you can modify some of the selected installation package’s settings by clicking the button Customize next to the Use package field.
The installation package’s settings will appear below and you can make the changes that you need. To find out more about editing installation packages, refer to Creating Installation Packages.
If you want to save the modifications as a new package, select the Save as package option placed at the bottom of the package settings list, and enter a name for the new installation package.
Click Save.
A confirmation message will appear.
You can view and manage the task in the Network > Tasks page.
If using VMware Horizon View Persona Management, it is recommended to configure Active Directory Group Policy to exclude the following Bitdefender processes (without the full path):
bdredline.exeepag.exeepconsole.exeepintegrationservice.exeepprotectedservice.exeepsecurityservice.exeepupdateservice.exeepupdateserver.exe
These exclusions must apply as long as the security agent runs on endpoint. For details, refer to this VMware Horizon documentation page.
Uninstall client
To remotely uninstall the Bitdefender protection:
Go to the Network page.
Select the container that you want from the left-side pane. All endpoints from the selected container are displayed in the right-side pane table.
Select the check boxes of endpoints from which you want uninstall the Bitdefender security agent.
Click the
 Tasks button at the upper side of the table and choose Uninstall client.
Tasks button at the upper side of the table and choose Uninstall client.A configuration window is displayed, allowing you to opt for keeping the quarantined items on the client machine.
Click Save to create the task. A confirmation message will appear.
You can view and manage the task on the Network > Tasks page. For more information, refer to Viewing and managing tasks.
Note
If you want to reinstall protection, be sure to restart the computer first.
Update client
Check the status of managed computers periodically. If you notice a computer with security issues, click its name to display the Information page. For more information, refer to Checking the endpoint status.
Outdated clients or outdated security content represent security issues. In these cases, you should run an update on the corresponding computer. This task can be done locally from the computer, or remotely from Control Center.
To remotely update the client and the security content on managed computers:
Go to the Network page.
Select the container that you want from the left-side pane. All endpoints from the selected container are displayed in the right-side pane table.
Select the check boxes of endpoints where you want to run a client update.
Click the
 Tasks button at the upper side of the table and choose Update. A configuration window will appear.
Tasks button at the upper side of the table and choose Update. A configuration window will appear.You can choose to update only the product, only the security content or both.
Click Update to run the task. A confirmation message will appear.
You can view and manage the task on the Network > Tasks page. For more information, refer to Viewing and managing tasks.
Page Menu
- Bitdefender – GravityZone
- Threats Xplorer
- Deleting endpoints
- Using Recovery Manager for encrypted volumes
- Assigning policies
- Creating quick reports
- Running tasks
- Viewing and managing tasks
- Sorting, filtering and searching for endpoints
- Organizing endpoints into Groups
- Viewing endpoint details
- Checking the endpoints status
- Network inventory
- Endpoint types
- Add Mailbox
- Configure Email
- Whitelist Email
- Install security agents – use cases
- Bitdefender Endpoint Security Tools for Linux quick start guide
- AD Connect
- Install Security Server manually
- Install security agents – standard procedure
- Install Security Server through Control Center
- Allow file download blocked by Bitdefender
- Email Security Licensing & Provisioning
- Check my monthly subscription for Bitdefender Security for AWS
- Viewing notifications
- Notification types
- Notifications
- Printing reports
- Emailing reports
- Saving reports
- Taking report-based actions
- Configuring notification settings
- Deleting notifications
- Create reports
- Report types
- Reports
- Executive Summary
- Announcements
- Viewing and managing scheduled reports
- Best practices
- Operation
- Operation
- Configuration
- Reconfigure client
- Repair client
- Restart machine
- Features distribution
- Network discovery
- Container Protection
- Update client
- Security for Storage
- Uninstall client
- eXtended Detection and Response (XDR)
- Install
- Endpoint Risk Analytics (ERA)
- Patch tasks
- Sandbox Analyzer
- Exchange scan
- Security for Exchange
- Deleting policies
- Full Disk Encryption
- Scan
- Email Security
- Scan for IOC
- Risk scan
- Device Control
- Computer policies
- Patch Management
- Renaming policies
- Network Attack Defense
- Changing policy settings
- Content Control
- Configuring profiles
- Firewall
- Assigning policies
- Advanced Anti-Exploit
- Creating policies
- HyperDetect
- Troubleshooting
- Advanced Threat Control
- Patch tasks
- Antimalware
- Credentials Manager
- Introduction
- Best practices