To remotely run a scan task on one or several endpoints:
Go to the Network page.
Select the container that you want from the left-side pane. All endpoints from the selected container are displayed in the right-side pane table.
Select the check boxes of endpoints or groups you want to scan.
Click the
 Tasks button at the upper side of the table and choose Scan.
Tasks button at the upper side of the table and choose Scan.A configuration window will appear.
Configure the scan options:
In the General tab, you can choose the type of scan and you can enter a name for the scan task.
The scan task name is intended to help you easily identify the current scan in the Tasks page.

Select the type of scan from the Type menu:
Quick scan uses in-the-cloud scanning to detect malware running in the system. This type of scan is preconfigured to allow scanning only critical Windows and Linux system locations. Running a Quick Scan usually takes less than a minute and uses a fraction of the system resources needed by a regular virus scan.
When malware or rootkits are found, Bitdefender automatically proceeds with disinfection. If, for any reason, the file cannot be disinfected, then it is moved to quarantine. This type of scanning ignores suspicious files.
Full scan checks the entire system for all types of malware threatening its security, such as viruses, spyware, adware, rootkits and others.
Bitdefender automatically tries to disinfect files detected with malware. In case malware cannot be removed, it is contained in quarantine, where it cannot do any harm. Suspicious files are being ignored. If you want to take action on suspicious files as well, or if you want other default actions for infected files, then choose to run a Custom Scan.
Memory scan checks the programs running in the endpoint’s memory.
Network scan is a type of custom scan, allowing to scan network drives using the Bitdefender security agent installed on the target endpoint.
For the network scan task to work:
You need to assign the task to one single endpoint in your network.
You need to enter the credentials of a user account with read/write permissions on the target network drives, for the security agent to be able to access and take actions on these network drives. The required credentials can be configured in the Target tab of the tasks window.
Custom scan allows you to choose the locations to be scanned and to configure the scan options.
For memory, network and custom scans, you have also these options:
Run the task with low priority. Select this check box to decrease the priority of the scan process and allow other programs to run faster. This will increase the time needed for the scan process to finish.
Note
This option applies only to Bitdefender Endpoint Security Tools.
Shut down computer when scan is finished. Select this check box to turn off your machine if you do not intend to use it for a while.
Note
This option applies to Bitdefender Endpoint Security Tools and Endpoint Security for Mac.
Note
These two options apply only to Bitdefender Endpoint Security Tools.
For custom scans, configure the following settings:
Go to the Options tab to set the scan options.
Click the security level that best suits your needs (Aggressive, Normal or Permissive).
Use the description on the right-side of the scale to guide your choice.
Based on the selected profile, the scan options in the Settings section are automatically configured. However, if you want to, you can configure them in detail. To do that, select the Custom check box and then expand the Settings section.

The following options are available:
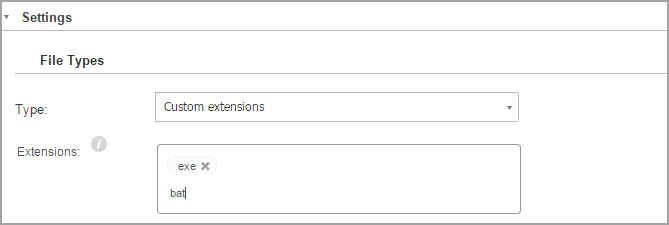
File types
Use these options to specify which types of files you want to be scanned.
You can set the security agent to scan all files (regardless of their file extension), application files only or specific file extensions you consider to be dangerous.
Scanning all files provides best protection, while scanning applications only can be used to perform a quicker scan.
Note
Application files are far more vulnerable to malware attacks than other types of files.
For more information, refer to Application file types.
If you want only specific extensions to be scanned, choose Custom extensions from the menu and then enter the extensions in the edit field, pressing
Enterafter each extension.Important
Bitdefender security agents installed on Windows and Linux operating systems scan most of the .ISO formats, but does not take any action on them.

Archives
Archives containing infected files are not an immediate threat to system security.
The malware can affect the system only if the infected file is extracted from the archive and executed without having real-time protection enabled.
However, it is recommended to scan archives in order to detect and remove any potential threat, even if it is not an immediate threat.
Important
Scanning archived files increases the overall scanning time and requires more system resources.
Scan inside archives
Select this option if you want to check archived files for malware.
If you decide on using this option, you can configure the following optimization options:
Limit archive size to (MB)
You can set a maximum accepted size limit of archives to be scanned.
Select the corresponding check box and type the maximum archive size (in MB).
Maximum archive depth (levels)
Select the corresponding check box and choose the maximum archive depth from the menu.
For best performance choose the lowest value, for maximum protection choose the highest value.
Scan email archives
Select this option if you want to enable scanning of email message files and email databases, including file formats such as .eml, .msg, .pst, .dbx, .mbx, .tbb and others.
Important
Email archive scanning is resource intensive and can impact system performance.
Miscellaneous
Select the corresponding check boxes to enable the desired scan options.
Scan boot sectors
Scans the system’s boot sector.
This sector of the hard disk contains the necessary computer code to start the boot process.
When a virus infects the boot sector, the drive may become inaccessible and you may not be able to start your system and access your data.
Scan registry
Select this option to scan registry keys.
Windows Registry is a database that stores configuration settings and options for the Windows operating system components, as well as for installed applications.
Scan for rootkits
Select this option to scan for glossary.rootkit rootkits and objects hidden using such software.
Scan for keyloggers
Select this option to scan for glossary.keylogger keylogger software.
Scan network shares
This option scans mounted network drives.
For quick scans, this option is deactivated by default. For full scans, it is activated by default. For custom scans, if you set the security level to Aggressive/Normal, the Scan network shares option is automatically enabled. If you set the security level to Permissive, the Scan network shares option is automatically disabled.
Scan memory
Select this option to scan programs running in the system’s memory.
Scan cookies
Select this option to scan the cookies stored by browsers on the computer.
Scan only new and changed files
By scanning only new and changed files, you may greatly improve overall system responsiveness with a minimum trade-off in security.
Scan for Potentially Unwanted Applications (PUA)
A Potentially Unwanted Application (PUA) is a program that may be unwanted on the PC and sometimes comes bundled with freeware software. Such programs can be installed without the user’s consent (also called adware) or will be included by default in the express installation kit (ad-supported). Potential effects of these programs include the display of pop-ups, installing unwanted toolbars in the default browser or running several processes in the background and slowing down the PC performance.
Scan detachable volumes
Actions
Depending on the type of detected file, the following actions are taken automatically:
When an infected file is found
Bitdefender detects files as infected through various advanced mechanisms, which include malware signatures, machine learning and artificial intelligence (AI) based technologies.
The Bitdefender security agent can normally remove the malware code from an infected file and reconstruct the original file. This operation is known as disinfection.
By default, if an infected file is detected, the Bitdefender security agent will automatically attempt to disinfect it.
If disinfection fails, the file is moved to quarantine in order to contain the infection.
Important
For particular types of malware, disinfection is not possible because the detected file is entirely malicious. In such cases, the infected file is deleted from the disk.
When a suspect file is found
Files are detected as suspicious by the heuristic analysis and other Bitdefender technologies.
These provide a high detection rate, but the users must be aware of certain false positives (clean files detected as suspicious) in some cases.
Suspect files cannot be disinfected, because no disinfection routine is available.
Scan tasks are configured by default to ignore suspect files.
You may want to change the default action in order to move suspect files to quarantine.
Quarantined files are sent for analysis to Bitdefender Labs on a regular basis.
If malware presence is confirmed, a signature is released to allow removing the malware.
When a rootkit is found
Rootkits represent specialized software used to hide files from the operating system.
Though not malicious in nature, rootkits are often used to hide malware or to conceal the presence of an intruder into the system.
Detected rootkits and hidden files are ignored by default.
Though not recommended, you can change the default actions.
You can specify a second action to be taken if the first one fails and different actions for each category.
Choose from the corresponding menus the first and the second action to be taken on each type of detected file.
The following actions are available:
Disinfect
Remove the malware code from infected files.
It is recommended to always keep this as the first action to be taken on infected files.
Move files to quarantine
Move detected files from their current location to the quarantine folder.
Quarantined files cannot be executed or opened; therefore, the risk of getting infected disappears.
You can manage quarantine files from the quarantine Quarantine page of the console.
Delete
Delete detected files from the disk, without any warning.
It is advisable to avoid using this action.
Ignore
No action will be taken on detected files. These files will only appear in the scan log.
Go to Target tab to configure the locations you want to be scanned on the target endpoints.
In the Scan target section you can add a new file or folder to be scanned:
Choose a predefined location from the drop-down menu or enter the Specific paths you want to scan.
Specify the path to the object to be scanned in the edit field.
If you have chosen a predefined location, complete the path as needed.
For example, to scan the entire
Program Filesfolder, it suffices to select the corresponding predefined location from the drop-down menu.To scan a specific folder from
Program Files, you must complete the path by adding a backslash (\) and the folder name.If you have chosen Specific paths, enter the full path to the object to be scanned.
It is advisable to use system variables (where appropriate) to make sure the path is valid on all target computers. For more information regarding system variables, refer to appendices.variables.
Click the corresponding add_inline.png Add button.
To edit an existing location, click it.
To remove a location from the list, click the corresponding elete_inline.png Delete button.
For network scan tasks, you need to enter the credentials of a user account with read/write permissions on the target network drives, for the security agent to be able to access and take actions on these network drives.
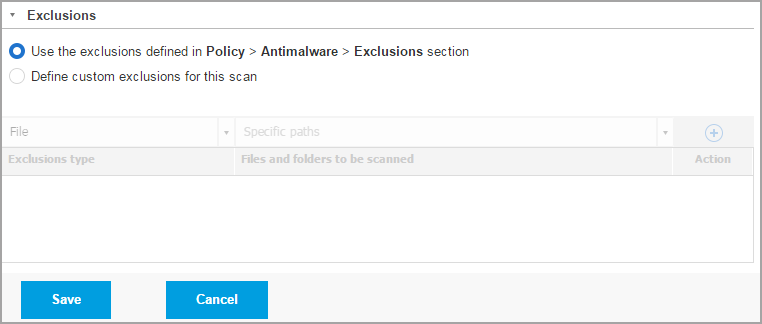
Click the Exclusions section if you want to define target exclusions.

You can either use the exclusions defined by policy or define explicit exclusions for the current scan task.
For more details regarding exclusions, refer to Settings.
Click Save to create the scan task. A confirmation message will appear.
You can view and manage the task on the Network > Tasks page. For more information, refer to Viewing and managing tasks.
Note
To schedule a scan task, go to the Policies page, select the policy assigned to the computers you are interested in, and add a scan task in the Antimalware > On-demand section. For more information, refer to On-demand.
Scan for IOC
At any time, you can choose to run on-demand scanning for known Indicators of Compromise (IOC) on selected endpoints.
Important
This task is only available for plans that include the EDR feature.
Go to the Network page.
Browse the containers and select the endpoints you want to scan.
Click the
 Tasks button and choose Scan for IOC.
Tasks button and choose Scan for IOC.A configuration page will appear, where you need to select the type of indicators taken into account for IOC scanning.

Important
You must select at least one type of Indicator of Compromise to create a valid task.
Select one or more IOC types you want to take into account for scanning and write the known IOC name in the newly added field.

You can select from the following types:
MD5
SHA1
SHA256
SHA512
File names
Process names
Registry values
Registry keys
Note
Content added inside each field must be valid. You will be prompted a warning sign and message if otherwise.
Click Save to create and run the Scan for IOC task.
A confirmation message will appear.
You can check the task’s progress in the Network > Tasks page.

Once the task has finished successfully you can click the
 Reports button to read the generated report and assess the impact of the scanned-for IOC.
Reports button to read the generated report and assess the impact of the scanned-for IOC.
Valid file extensions for IOCs added to the task include: exe, dll, com, scr, jar, msi, msc, bat, ps1, vbs, vbe, js, jse, wsf, wsh, psc1, lnk, doc, docx, docm, xls, xlsx, xlsm, ppt, pptx, pptm, eml, rtf, pdf, html, ppsx, pps, ppsm, pot, potx, potm, ocx, sys, fnr, fne, and pif.
The Scan for IOC task will scan the following locations.
%Windows%\System32\Drivers%Windows%\System32\WindowsPowerShell\v1.0%Windows%\system32\config\systemprofile\AppData%Windows%\System32\Tasks%Windows%\System32\wbem%Windows%\SysWOW64\WindowsPowerShell\v1.0%Windows%\SysWOW64\config\systemprofile\AppData%Windows%\SysWOW64\sysprep%Windows%\Scripts%Windows%\System%Windows%\Web%Users%
Important
The Scan for IOC tasks will not run / will fail on endpoints in the following situations:
The endpoint does not have a Windows operating system.
The endpoint’s Bitdefender agent license is invalid.
The EDR module is not installed in the security agent installed on the target endpoints.
More than 100 Scan for IOC tasks are currently in queue.
Invalid data is entered by user in the Scan for IOC task configuration page.
Page Menu
- Bitdefender – GravityZone
- Threats Xplorer
- Deleting endpoints
- Using Recovery Manager for encrypted volumes
- Assigning policies
- Creating quick reports
- Running tasks
- Viewing and managing tasks
- Sorting, filtering and searching for endpoints
- Organizing endpoints into Groups
- Viewing endpoint details
- Checking the endpoints status
- Network inventory
- Endpoint types
- Add Mailbox
- Configure Email
- Whitelist Email
- Install security agents – use cases
- Bitdefender Endpoint Security Tools for Linux quick start guide
- AD Connect
- Install Security Server manually
- Install security agents – standard procedure
- Install Security Server through Control Center
- Allow file download blocked by Bitdefender
- Email Security Licensing & Provisioning
- Check my monthly subscription for Bitdefender Security for AWS
- Viewing notifications
- Notification types
- Notifications
- Printing reports
- Emailing reports
- Saving reports
- Taking report-based actions
- Configuring notification settings
- Deleting notifications
- Create reports
- Report types
- Reports
- Executive Summary
- Announcements
- Viewing and managing scheduled reports
- Best practices
- Operation
- Operation
- Configuration
- Reconfigure client
- Repair client
- Restart machine
- Features distribution
- Network discovery
- Container Protection
- Update client
- Security for Storage
- Uninstall client
- eXtended Detection and Response (XDR)
- Install
- Endpoint Risk Analytics (ERA)
- Patch tasks
- Sandbox Analyzer
- Exchange scan
- Security for Exchange
- Deleting policies
- Full Disk Encryption
- Scan
- Email Security
- Scan for IOC
- Risk scan
- Device Control
- Computer policies
- Patch Management
- Renaming policies
- Network Attack Defense
- Changing policy settings
- Content Control
- Configuring profiles
- Firewall
- Assigning policies
- Advanced Anti-Exploit
- Creating policies
- HyperDetect
- Troubleshooting
- Advanced Threat Control
- Patch tasks
- Antimalware
- Credentials Manager
- Introduction
- Best practices